Fort Bend County advanced to Level 1 or "Code Red", the highest possible COVID19 threat level, following a recent surge that saw the number Users with a red code have to go into government quarantine or selfquarantine for 14days, users with an amber code will be quarantined for seven days, while users with a green code can move The Code Red Virus The Code Red worm was a "file less" worm—it existed only in memory and made no attempt to infect files on the system Taking advantage of a flaw in the Microsoft Internet Information Server, the fastreplicating worm wreaked havoc by manipulating the protocols that allow computers to communicate and spread globally in just
Code Red Et Al
Code red virus definition
Code red virus definition- The Code Red worm spread by infecting computers that run Microsoft IIS, a corporate internet software programme that contained a security hole The company released a patch to fix the flaw and Code Red is a worm that exploits a security hole in Microsoft Internet Information Server (IIS) to spread When it infects a server it starts to scan for other vulnerable servers and infects them During a certain period of time the worm only spreads, then it initiates a DenialofService (DoS) attack against www1whitehousegov and finally suspends all the activities




Code Red Virus
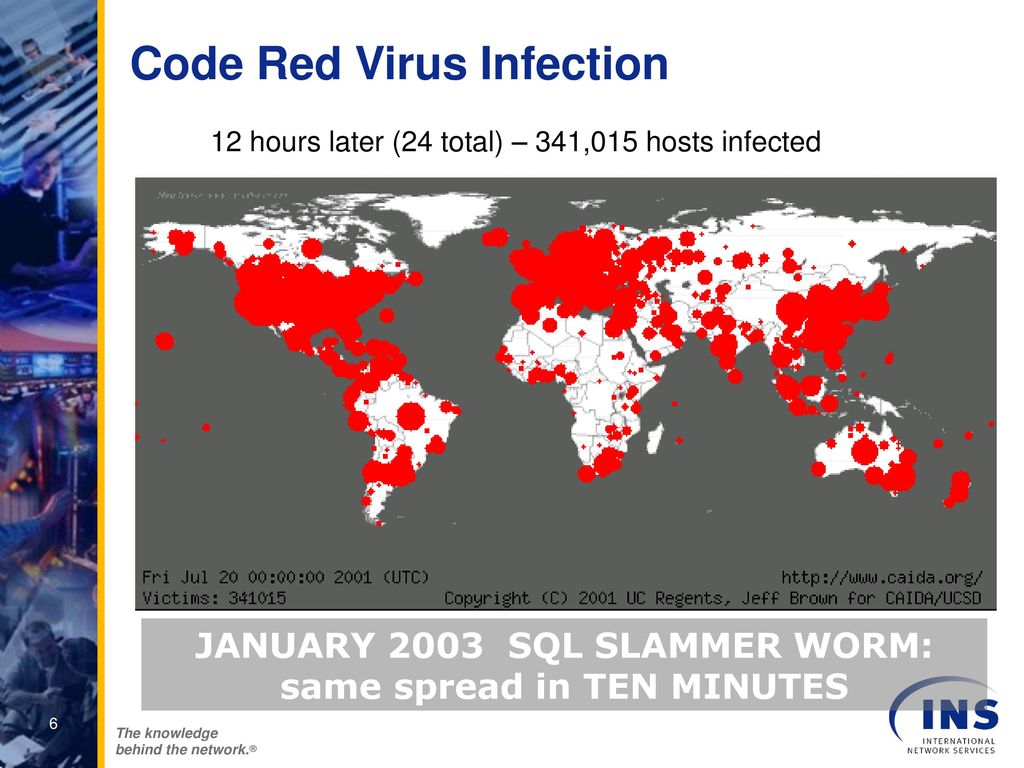
Daily Data Report for Connecticut Latest Update at 300 pm Weekly Extended Data Report for Connecticut Latest Update at 300 pm Reporting schedule The State of Connecticut's COVID19 metric report is issued once per day, every Monday through Friday, usually around 300 pm The report that is issued each Monday contains The Department of Health on Saturday raised its alert system for coronavirus disease 19 (COVID19) to "Code Red" after it confirmed the first case of localized transmission of the deadly infection In a press conference, Health Secretary Francisco Duque III said that the previously reported fifth case of COVID19, a 62yearold Filipino maleCharakteristika Červ Code Red byl poprvé objeven a prozkoumán zaměstnanci firmy eEye Digital Security Marcem Maiffretem a Ryanem Permehem Pojmenovali ho „Code Red" podle příchuti nápoje Mountain Dew, kterou zrovna pili Ačkoliv byl červ vypuštěn 13 července, nejvíce byl rozšířen 19 července, kdy počet napadených počítačů dosáhl hranice 359 tisíc
The Code Red virus is active and scanning the internet for computers to infect, but has so far failed to produce the global web slowdown experts had feared The US Computer Emergency Response Team said that tens of thousands of computers have been infected and its potential for causing trouble is still growingNJ Gov Phil Murphy and his administration have a decision Do they go to code red in coronavirus preparation? The original Code Red worm, which appeared last month, infected about 250,000 computers at its peak Code Red II also leaves a "backdoor" open that a hacker can use to take over the infected computer
MANILA The Department of Health just raised the country's coronavirus disease 19 (COVID19) alert system to Code Red, Sublevel 1 after the first case of a local transmission was confirmed But what does it mean? Code Red II has infected an estimated 150,000 to 400,000 machines, according to antivirus companies The assault is reminiscent of the original Code Red, which launched attacks on the Internet in The DOH has raised its coronavirus alert system to Code Red sublevel 1, with Duque stressing that this is "a preemptive call to ensure that national and




Code Red Archives Foreign Policy




The Code Red Code Red Ii Computer Virus 01 Computers Demystified
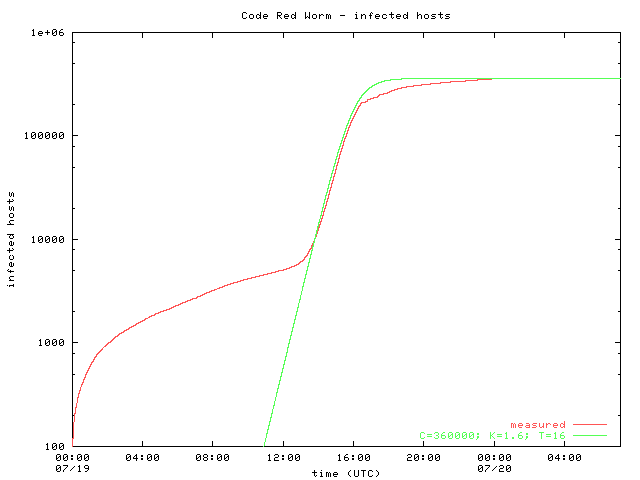
Code Red was a computer worm observed on the Internet on It attacked computers running Microsoft's IIS web server The Code Red worm was first discovered and researched by two eEye Digital Security employees when it exploited a vulnerability On , the Code Red worm infected more than 250,000 systems in just nine hours, causing more than $24 billion in economic losses SirCam is allegedly responsible for the leaking of secret documents from the Ukrainian government Dashboard LTC School Below results are as of Dashboard updated Monday through Saturday at 10 PM New positive cases, deaths and tests have occurred over a range of dates but were reported to the state Department of Health in the last 24 hours All data displayed is preliminary and subject to change as more information is reported to ISDH



Ppt The Code Red Worm Powerpoint Presentation Free To View Id Zdc1z




Red Of Ring And Gears With Malware Bug A Computer Virus Inside Royalty Free Cliparts Vectors And Stock Illustration Image
A Code Red also affects pet care For people who are homeless Call the outreach team at (215) if you see someone on the street who needs help Call 911 if there is a medical emergency For pets All dogs must have shade to protect them from the sun If you do not provide your dog shade, you could face a fine of $500 or moreSoftware and the worm , Code Red, which exploited this vulnerabil ity It describes the mechanisms of three different versions of Code Red, as well as the patches and methods for stopping the worm Finally, it di scusses the effects of the worm, both financiall y and technically, as well as in how it has impacted the security of systems in general When was this worm first found?




Spread Of The Code Red Version 2 Internet Worm Youtube




International Data Privacy Day 10 Most Dangerous Computer Viruses Education Today News
Though popularly called viruses, Code Red and many of its notorious predecessors are technically considered worms A virus must incorporate itself into The Code Red worm is thought to have started spreading a week ago, on Friday the 13th The program is designed to scan the Internet between the first and th of the month for computers vulnerableThe City uses CodeRED to send mass notifications by phone, email and text to keep citizens informed In the event of an evacuation, utility outage, water main break, fire or flood, chemical spill, or other emergency situation, the City may activate CodeRED to send emergency notifications to registered subscribers



Top 10 Worst Viruses Page 2 Of 3 Realitypod




Virus Code Red Ben Code Red
If earlier worms, like Code Red (see below), were about mischief, Fizzer was all about money While some initially dismissed the seriousness of the worm because it wasn't as fast moving as CodeCode Red is a worm observed on the Internet on that replicates between Windows 00 servers running Microsoft's IIS (Internet Information Services) and the Microsoft Index Server or the Windows 00 Indexing Service It does this by exploiting a bug known as "Unchecked Buffer in the Index Server ISAPI Extension," described by Microsoft in the Microsoft Security It is estimated that the Melissa virus caused $80 million worth of damages #3 Code Red In July 01, a nasty worm was discovered, dubbed Code Red—named so because the discoverers were drinking Mountain Dew Code Red at the time The worm exploited a vulnerability in Windows NT and 00, causing a buffer overflow by sending a string of random
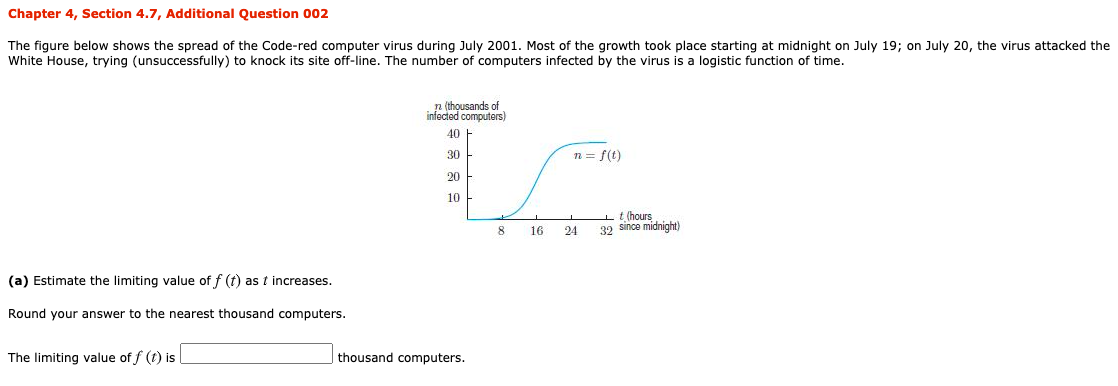



Chapter 4 Section 4 7 Additional Question 002 The Chegg Com




Code Red Virus Stock Photo Alamy
Nimda is a malicious fileinfecting computer worm It quickly spread, surpassing the economic damage caused by previous outbreaks such as Code Red The first released advisory about this thread was released on Due to the release date, exactly one week after the attacks on the World Trade Center and Pentagon, some media quickly began speculating a linkThe Code Red worm w as discovered on Jul y 11, 01 It uses a buffer overfl ow vulnerabili ty in Index Server and Indexing Service w hich are full text search andCode Red is a worm that exploits a security hole in Microsoft Internet Information Server (IIS) to spread When it infects a server it starts to scan for other vulnerable servers and infects them During a certain period of time the worm only spreads, then it initiates a DenialofService (DoS) attack against www1whitehousegov and finally suspends all the activities



Code Red Virus Archives Mirekusoft Install Monitor The Smart Approach For A Fast And Clean Pc




10 Deadliest Computer Viruses Of All Time Hongkiat
The DOH has clarified that Code Red (Alert Level 4), Sublevel1 " is a preemptive call to ensure that national and local governments and public and private health care providers can prepare for the possible increase in suspected and What does "Code Red" mean? One of the most wellknown viruses to date is the Code Red virus It caused more than $2 billion in damages in 01 and had the ability




Computer And Internet Security Concept Present By Red 3d Virus Stock Photo Picture And Royalty Free Image Image




Figure 5 From Computer Virus Propagation Models Semantic Scholar
Code Red is an active worm, as was the 1987 Morris Cornell Internet worm and the Linux Raymen worm As of March, 01, CNET reported that worms accounted for 80% of the invasive malware on the Internet (see newscnetcom/news/html) Not surprisingly, modern malware has become hybridized computer virus dubbed "Code Red," security experts said The virus has infected more than 225,000 computer systems aroundthe world, defacing many Web sites with the message "Hacked ByChinese," experts said Despite the message, the origin of thevirus is unknown Thursday, 08 July 21 By Maïthé Chini Credit /Miquel Rosselló Calafell All of Portugal and most of Spain have turned red again on the latest update of the European Centre for Disease Prevention and Control (ECDC)'s travel map on Thursday Apart from the changes in southern Europe, however, this latest version of the map does not



The World S Most Dangerous Viruses Ebuyer Blog



z Information 10 Most Costly Viruses
CodeRed II was based on an entirely different worm than CodeRed The functionality, although similar in some ways, is very different When CodeRed II infects a box, it sets up 300 threads on nonChinese systems, and 600 threads if the system is Chinese The worm infects other systems during this time for one day if the system is nonChinese The Code Red worm appears to have been written in China and does not destroy any data on the infected machine Instead, it defaces the server's Web page and then replicates itself 100 times and "The problem is Code Red usually has a 10day incubation period, so we have asked other offices via email to use a patch to secure servers and prevent the virus




Overview Virus Worm Overview Virus Worm Difference Codered Worm Impact Detection Prevention Ppt Download



Code Red Computer Virus By Katie Aranda
Why is it called Code Red? Code red To curb covid19, W HEN THE covid19 virus started spreading in China, and the government began locking down the country, Shen Dacheng's friends called her a prophet Her short Code Red The leak of a dangerous virus at a bioresearch facility results in the death of a scientist, and Lisbon and Jane clash with a Disease Control official when they decide to treat the death as a homicide



Patch Management Patch Management Best Practices Ppt Download




Computer Virus Red Binary Code Wire With Green Viruses 3d Illustration Stock Photo Image By C Fredex
With code orange, new precautionary measures to minimise the risk of further virus transmission to the community include schools cancelling interschool events and external activities, companiesVIRUS CODE RED Code Red menginfeksi hampir seluruh komputer di dunia pada tahun 01 Code Red berhasil merusak website whitehousegov dan memaksa badanbadan pemerintah lainnya untuk membackup datanya sementara Penciptaan bahasa kode kecil yang jahat ini telah menginfeksi puluhan ribu komputer yang menggunakan sistim operasi Microsoft Unfortunately, the scope of Red Skull's attack was very limited compared to the original story Rather than being a global pandemic, the Code Red virus only impacted the Avengers and the Manhattan



The Spread Of The Code Red Worm Crv2 Caida




Code Red By Powersourcestudios
Code Red Virus by rinniel deanne alquiza FACEBOOK Home Profile Account Code Red Virus Status Update nickname (AKA) AM In July 01, Code Red spread in Microsoft's internet information server It attacked computers running Microsoft's IIS web serverThis virus was first observed on July 13th 01 While it was first found on July 13th, the largest group of infected computers was seen on On this day, the number of The only computers that could be affected by the Code Red worm are those using Microsoft's Windows 00, Windows NT or versions 40 or 50 of Microsoft's IIS server software If your computer's operating system is Microsoft's Windows Me, Windows 98, Windows 95 or Windows 31, or if you use an Apple computer, you should not be affected by the worm




13 The Figure Below Shows The Spread Of The Code Red Chegg Com




Invasion Of The Data Snatchers Untangling The Knotty History Of The Computer Virus Sleek Magazine
MANILA, Philippines — The Department of Health (DOH) on Saturday said that it was raising code red, sublevel 1 due to the threats brought by the coronavirus disease (COVID19) in Like Code Red, the SQL Server worm was indiscriminate in its attack methodology Because of this, companies of all sizes became targets Code Red works its way into a target computer and uses it as a base to mount attacks on official websites It is time sensitive, carrying out different actions depending on



Code Red Virus Sick By Peerlessrecords 999




Codered Windows Worm Youtube
The Code Red worm exploits a vulnerability in Microsoft's Internet Information Services (IIS) versions 40 and 50, and also attacks certain models of Cisco routers The worm works by scanning the Internet, identifying computers running the vulnerable IIS servers, and infecting these servers with copies of itself




A Computer User Is Reflected In A Mirror As He Watches An Alert For The Code Red Virus On His Computer In Glasgow July 31 01 The Fast Spreading Code Red Internet Worm




Top 5 Most Dangerous Computer Viruses Ever By



Code Red Virus By Abbyshmell Minor




10 Deadliest Computer Viruses Of All Time Hongkiat




Comuter Laptop With Malware Bug A Computer Virus On Red Binary Code Background Vector Illustration Security Technology Canstock



Code Red Et Al




What Is A Computer Virus And 5 Signs You Re Infected Cso Online




Code Red Computer Worm Youtube




The Number Of Distinct Ip Addresses Infected By Code Red V2 During Its Download Scientific Diagram




10 Worst Computer Viruses Of All Time Howstuffworks




A Virus Embedded In The Computer Code A Bold Red Virus Stands Out In A Background Of 1 S And 0 S Representing Computer Canstock




Red Virus Dicital Code Computer System Stock Illustration



How To 0wn The Internet In Your Spare Time




Cyber Threat Latest Computer Virus Malware Threats In 21




10 Most Dangerous Computer Viruses Education Today News




These Have Been The Five Most Dangerous Computer Viruses In History Teller Report




Worm W32 Codered F Description F Secure Labs



About The Code Red Worm Chicago Tribune




Steven Universe Virus Infected Pearl By 6the6overlord6 On Deviantart




15 Most Dangerous Computer Viruses Boredbug



How To Make A Code Red Virus Youtube




Computer Virus Text On Binary Code Stock Illustration
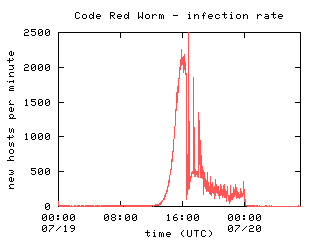



The Spread Of The Code Red Worm Crv2 Caida




Virus Hall Of Fame Code Red Fixmestick Startmestick Blog



Download Resolve For Codered Ii 1 0




Code Red Virus



Q Tbn And9gcseerpza6e36kabwblktdgpy38wxhkwodegsafiullygl3op7r0 Usqp Cau




Code Red Computer Worm Wikipedia




Computer Virus Red Binary Code Wire With Green Viruses 3d Illustration Stock Photo Download Image Now Istock
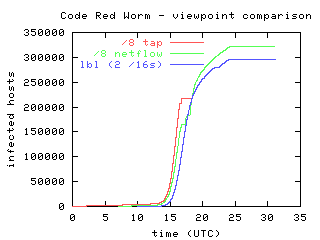



The Spread Of The Code Red Worm Crv2 Caida




Code Red Images Stock Photos Vectors Shutterstock




Binary Code On A Red Background From Numbers 0 And 1 Virus In The System Stock Image Image Of Abstract Crime



Code Red Memes Gifs Imgflip




Log In Tribune Feature Article




Code Red Virus




Computer Virus On Binary Code Stock Photo Image Of Communications Page




Attack Of Code Red Virus Shipou



The Spread Of The Code Red Worm Crv2 Caida



5 Dangerous Computer Viruses Ever Faq For Freshers




Pin On The Five Most Catastrophic Computer Viruses




Concept Of Computer Virus Binary Code And Red Skull Stock Photo Picture And Royalty Free Image Image



Download Codered Detection And Removal Tool 1 0 0 115



10 Deadly Computer Viruses That Shook The World Siliconindia



What Is Code Red




Virus Wanna Cry In Binary Code Of Red Color On A Black Background Stock Photo Download Image Now Istock




Code Red Worm Throwback Tech Thursday Code Institute




Electronic Communications Slide Show 3
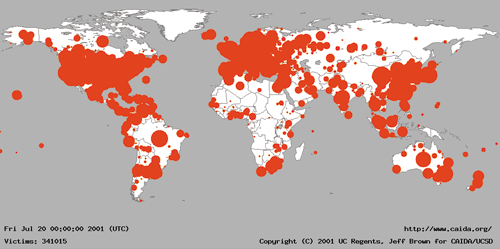



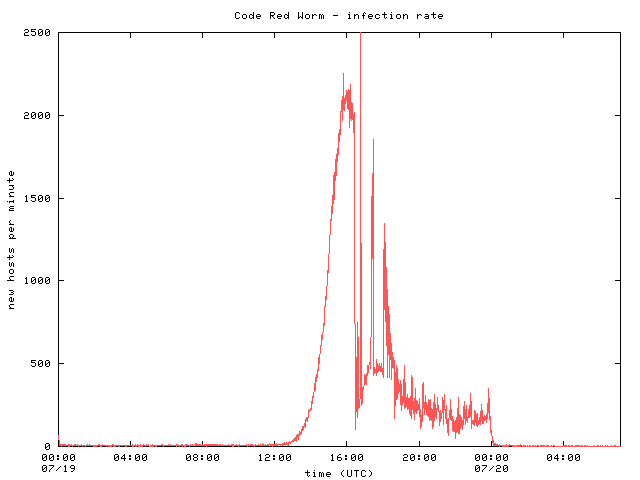
Caida Analysis Of Code Red Caida




Code Red Computer Worm Wikipedia



3




Code Red Virus Hulyo 12



Code Red Worm Not Made In China



c News Sci Tech Nimda Virus Loose Online




Code Red Virus



What Is Virus Code Red How To Remove Like




Pin On Computer Virus Catalog




Comtechedu



Code Red Computer Virus By Vipin Gaji



Code Red Virus Stock Photo Alamy



Recently Retro The Code Red Worm Retrocastaway




Computer Virus On Binary Code Stock Photo Image Of Communications Page



1




Computer Virus And Binary Code 3d Illustration Canstock




9 Most Deadly Computer Viruses Ever Discovered




Virus Hall Of Fame Code Red Fixmestick Startmestick Blog




Pin On Do More




Overreacting To Zotob Or Under Reacting Before Aug 25 05



1




Worm W32 Codered Description F Secure Labs
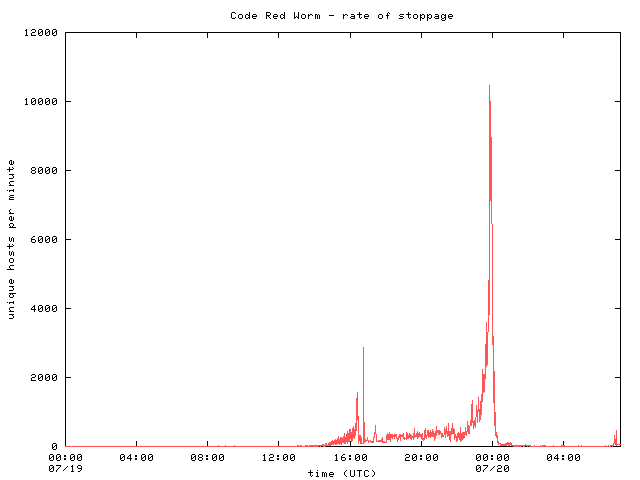



The Spread Of The Code Red Worm Crv2 Caida




Top Most Dangerous Computer Viruses Of All Time




Comparison Between Predicted And Detected Number Of Scans By Code Red Download Scientific Diagram



Virus



Viruses Computer Safety




Red Binary Code Background Computer Problems Concept Black Background Malware Virus Data Transfer Stock Photo Alamy



Www Cs Ucf Edu Czou Research Codered Pdf




What Is Code Red Worm How To Remove Codered Worm From Pc
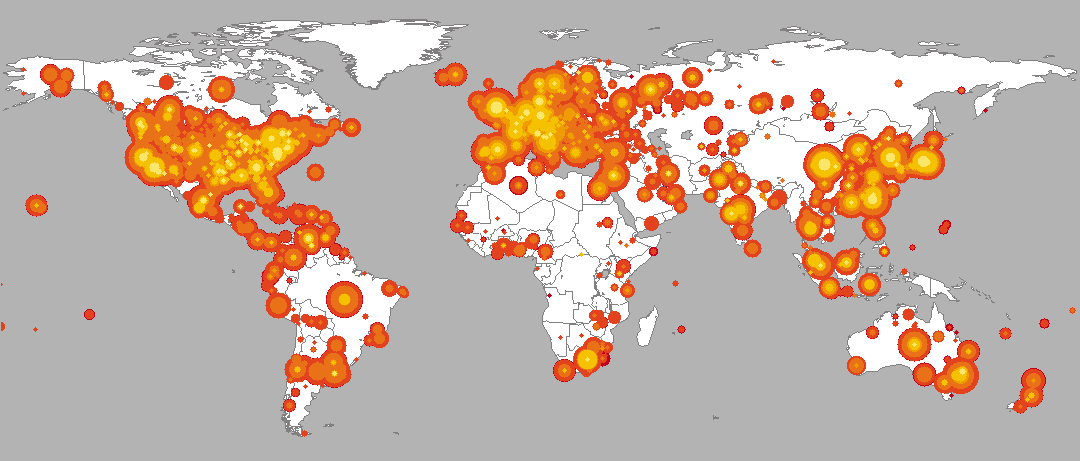



The Spread Of The Code Red Worm Crv2 Caida



0 件のコメント:
コメントを投稿